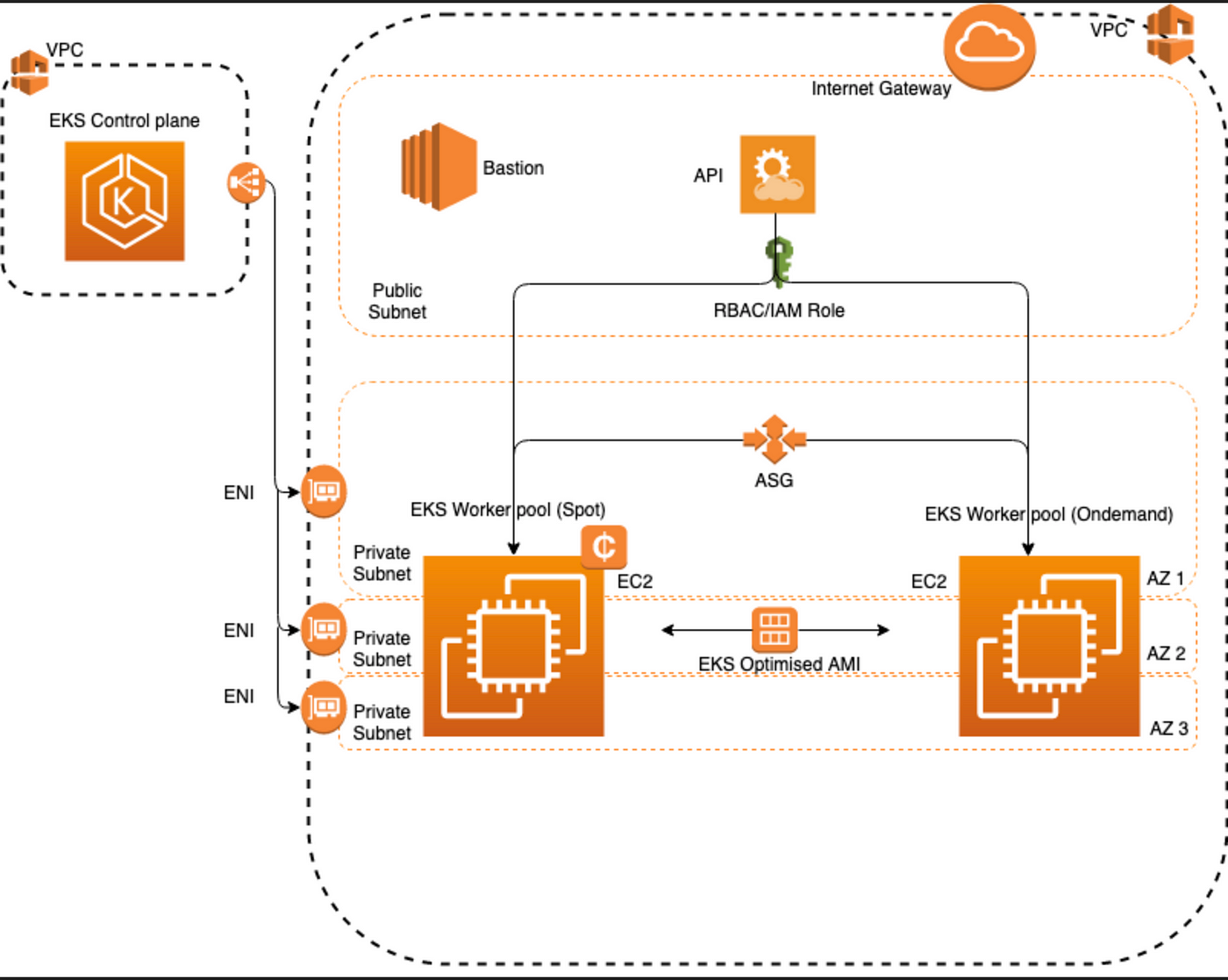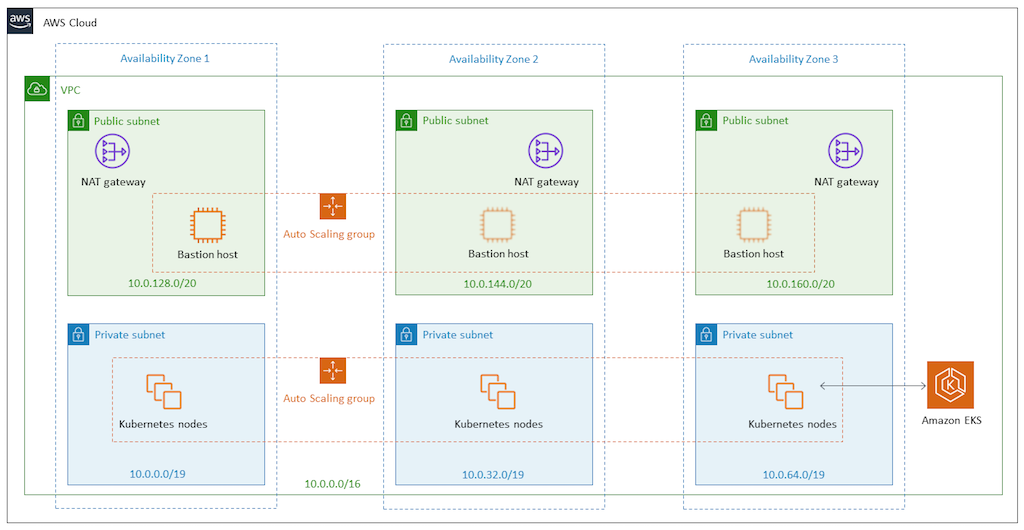
Deploy NetScaler VPX in active-active high availability in EKS environment using Amazon ELB and NetScaler Ingress Controller

Governance in kubernetes: How to enforce trusted images via OPA Gatekeeper in EKS | by Raphael Moraes | Webera
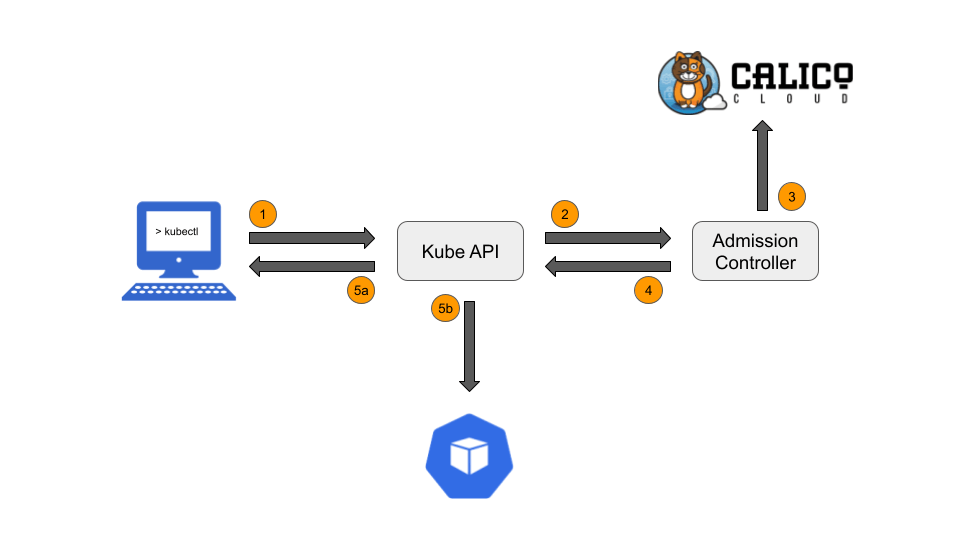
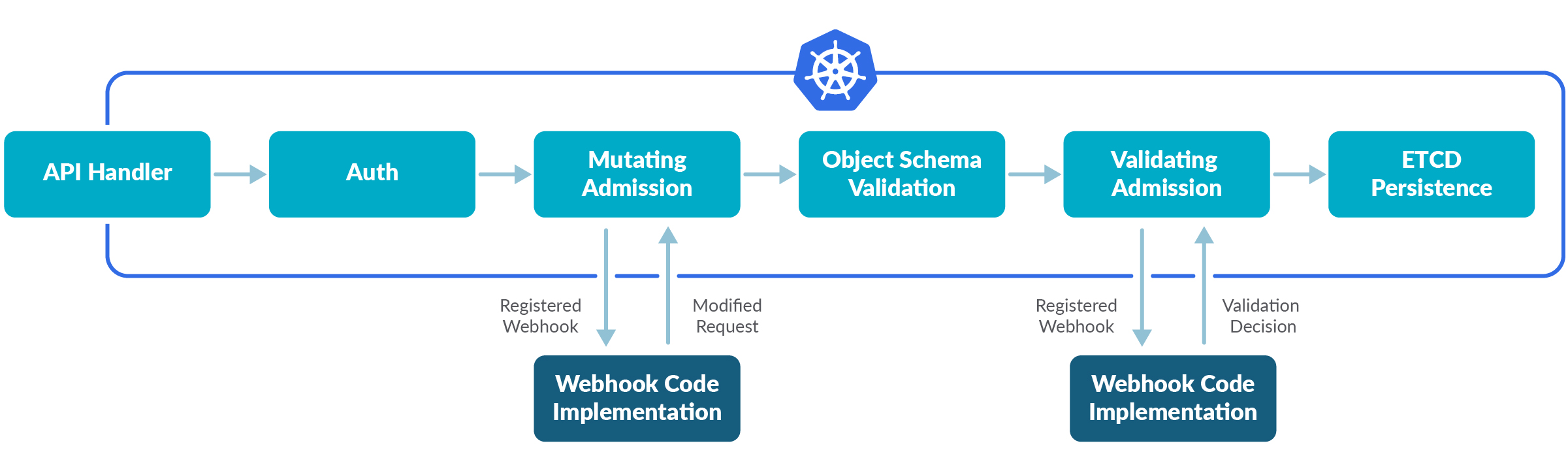
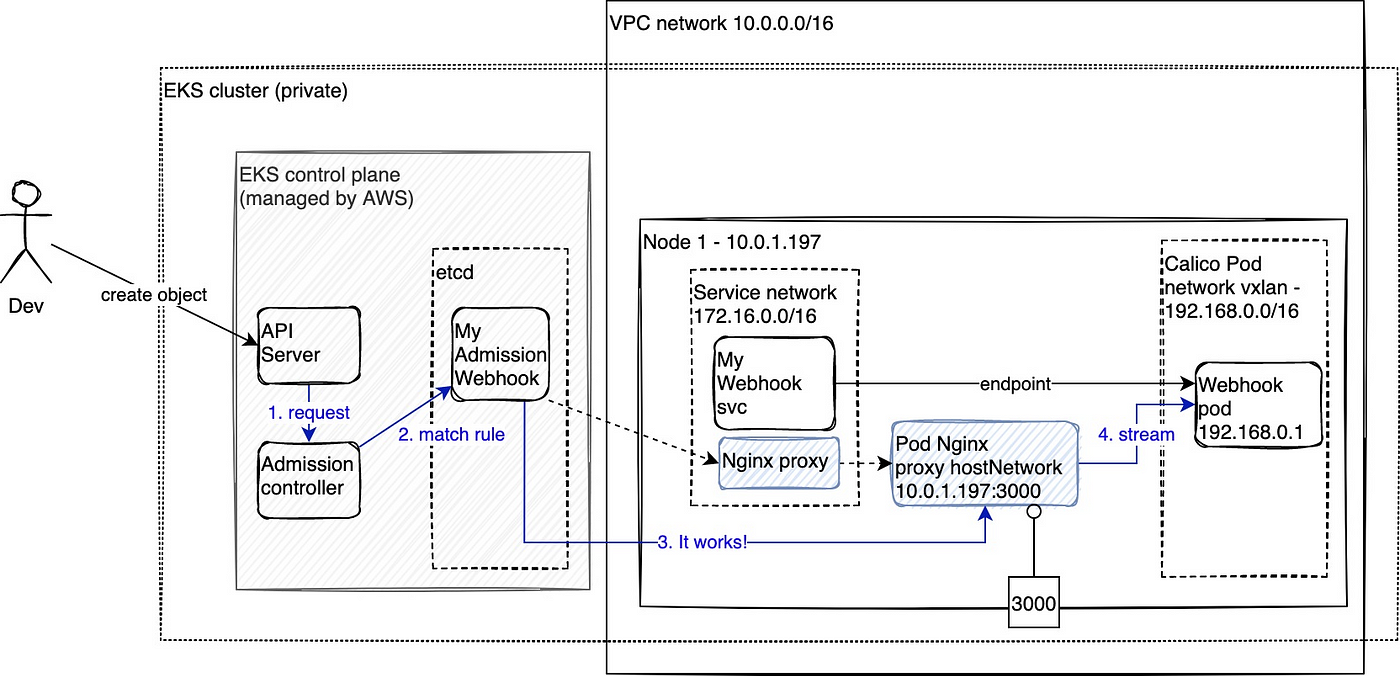
EKS] [request]: Allow specifying which admission controllers are enabled · Issue #739 · aws/containers-roadmap · GitHub

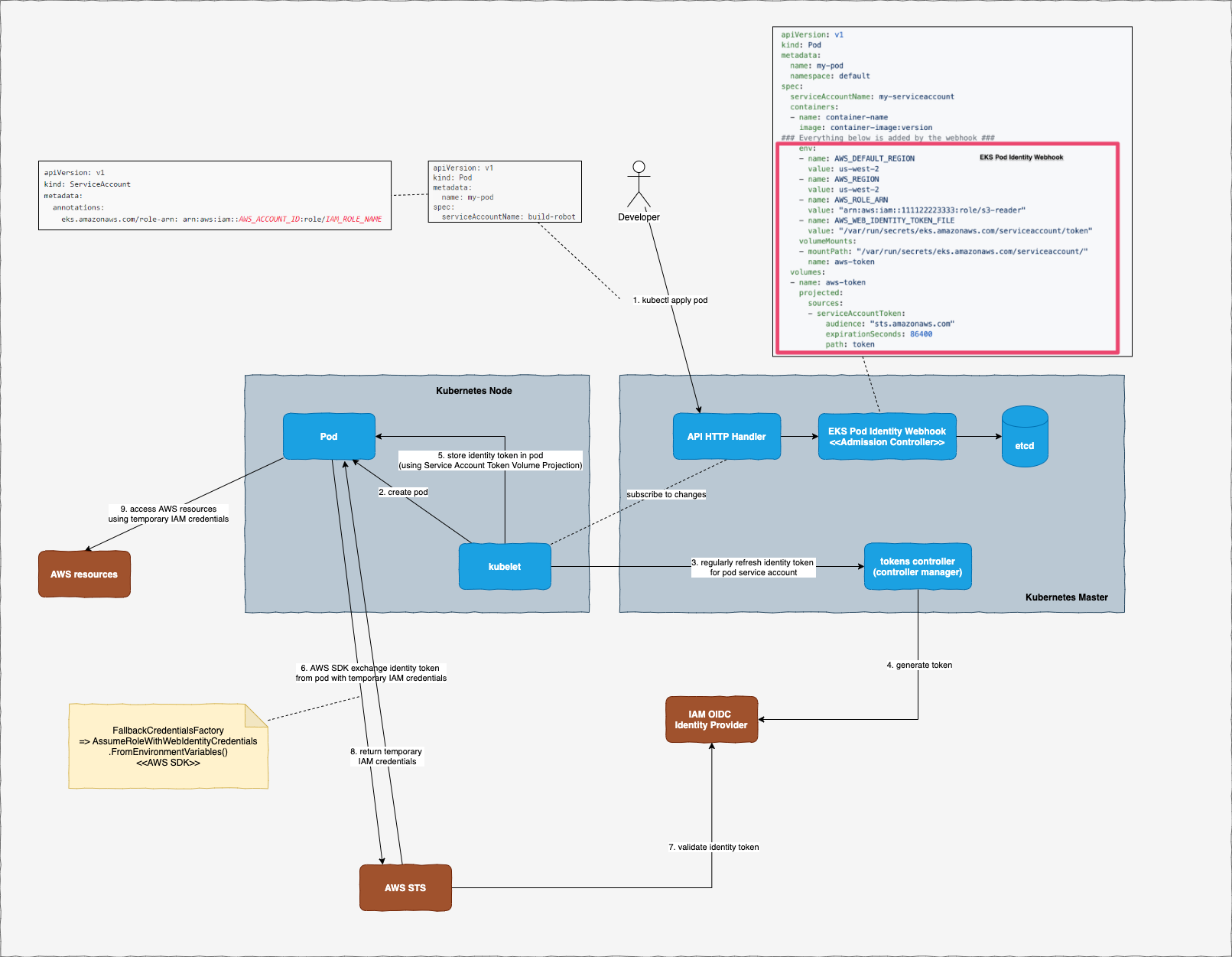
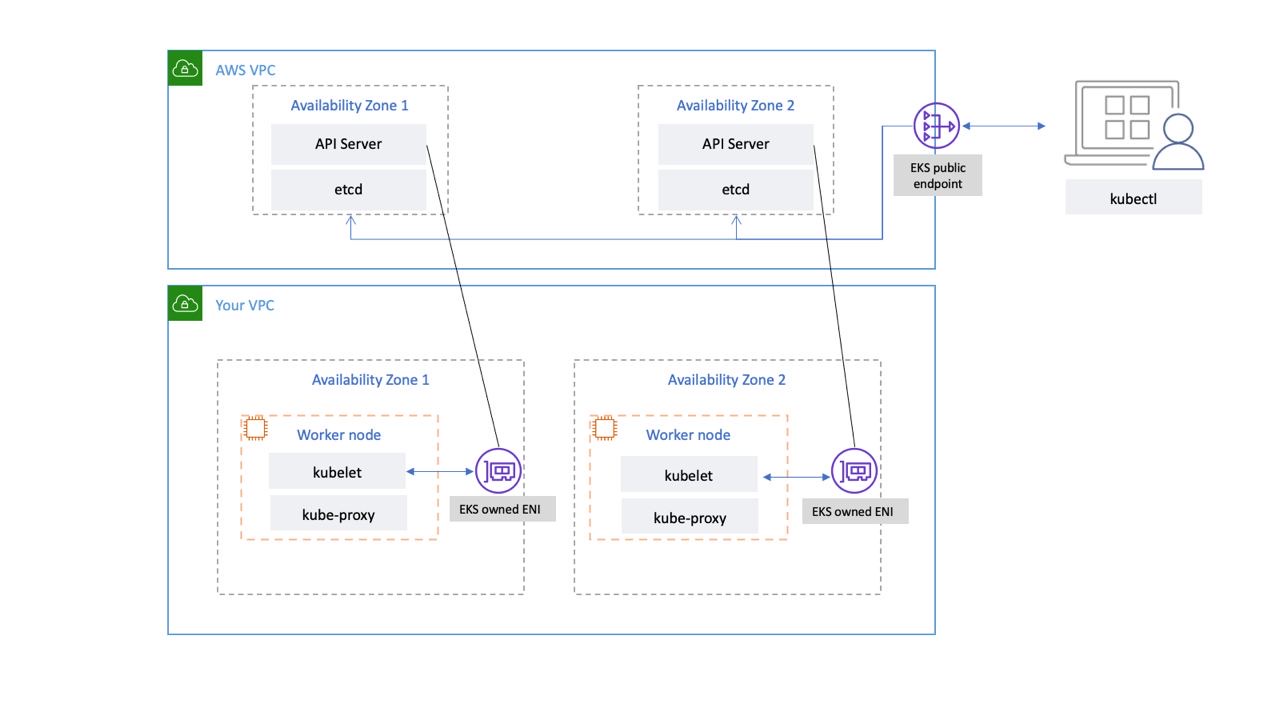
Attacking and securing cloud identities in managed Kubernetes part 1: Amazon EKS | Datadog Security Labs